 So now that we have prepared our IronKey device, prepared the Task Sequence Media and Windows To Go package we can have a look at the provisioning of IronKey with Windows To Go. What we need to do is to change the Task Sequence to enable BitLocker and we need to deploy the package so that we eventually are able to provision the device.
So now that we have prepared our IronKey device, prepared the Task Sequence Media and Windows To Go package we can have a look at the provisioning of IronKey with Windows To Go. What we need to do is to change the Task Sequence to enable BitLocker and we need to deploy the package so that we eventually are able to provision the device.
- Prepare the IronKey device
- Create a special task sequence for deploying your captured Windows 8.1 image
- Create a prestage media for the task sequence
- Create a Windows To Go creator package
- Update the task sequence to enable BitLocker
- Deploy the Windows To Go creator package and Windows 8.1 task sequence.
5. Update the task sequence to enable BitLocker
Since we do want to have the data also secure we want to update our Task Sequence to enable BitLocker on the IronKey device. You can find the odsbitlocker_wtg.exe file for the platform you need to support (x86 or x64) in OSDToolsBitLocker in Configuration Manager program folder. Copy the file to a new folder in your package source share and create a Package for this. Use for the Package in a Run Command Line task the following as the command line: osdbitlocker_wtg.exe /Enable /pwd:AD
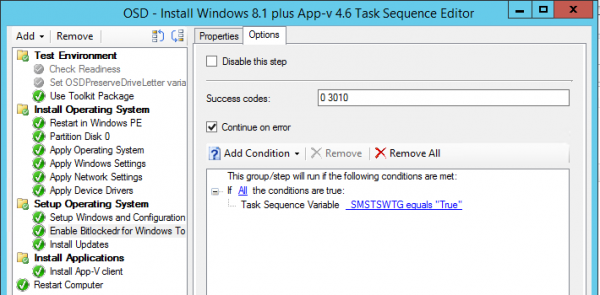
The /pwd parameter can either be None for not saving the passphrase or AD for storing the BitLocker Passphrase in Active Directory. I would always use AD 🙂 Next step is to distribute the package to your distribution points and update the task sequence so that we are able to enable BitLocker encryption on our Windows To Go devices.
The just created package must be added to the Task Sequence that you use to deploy your Corporate Windows 8.1 image. Ensure that you only run the package when the value of the Task Sequence variable _SMSTSWTG is equal to True.
For tasks especially for physical computers exclude tasks by setting the task sequence variable _SMSTSWTG is equal to False. You can use it for instance with a custom partitioning task.
So now that we are all set we need to deploy the created Windows To Go Creator Package to a collection with users that are allowed to provision the Windows To Go devices and deploy the Task Sequence to a collection to a Windows Device that is allowed to be used to provision the Windows To Go device, and deploy the task sequence to the All Unknown Computers collection.
6. Deploy the Windows To Go creator package and Windows 8.1 task sequence.
The name of step 6 is bot chosen well 😉 but let’s keep it this way since we will be in a way deploying both the package and the task sequence. BTW Be sure that the Task Sequence is deployed as required, otherwise the task sequence media will not pick up the task sequence. The first step of provisioning the device is to run the Windows To Go Creator package on the machine where plugged in the USB device. Of course we first need to unlock the device and enable the 2-lun mode.
When stating the application you see that you can select the unlocked partition of 28,7GB.
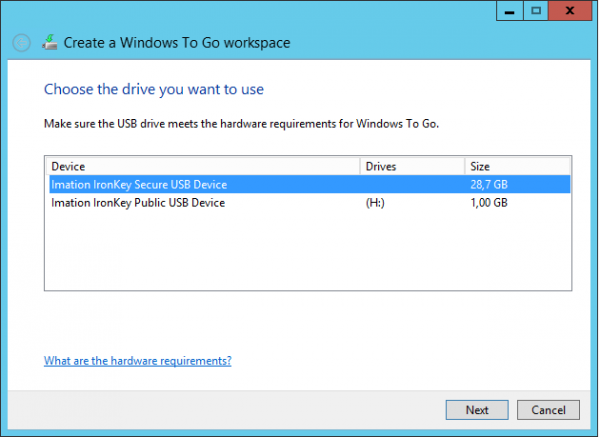
When clicking on Next you are able to Create the Windows To Go workspace on the IronKey Secure USB Device. The device will be formatted and provisioned with the Windows Image.
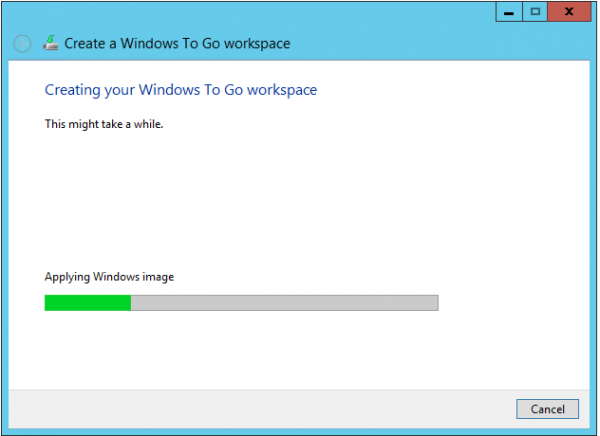
After the process is finished and the Windows To Go workspace is created we are ready for the next step, installing the captured image on the IronKey device. This is done by rebooting the machine with the USB key attached and be sure that the computer is in the collection where the task sequence is deployed to. Also be sure that you are able to boot from the USB device.
The first step is to unlock your device by entering your password / pin supplied in our first blog, By selecting Unlock, the device will be unlocked and a reboot will be initiated.
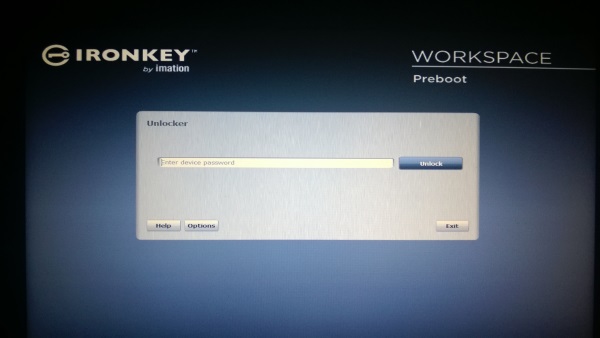
After rebooting the system be sure to boot from the USB device again. The system will boot into Windows PE and the IronKey device will be provisioned with the corporate Image. Be sure to use the key on a device that allows BitLocker. During this process the computer will be booting a couple of times so be sure to boot from USB every time 😉
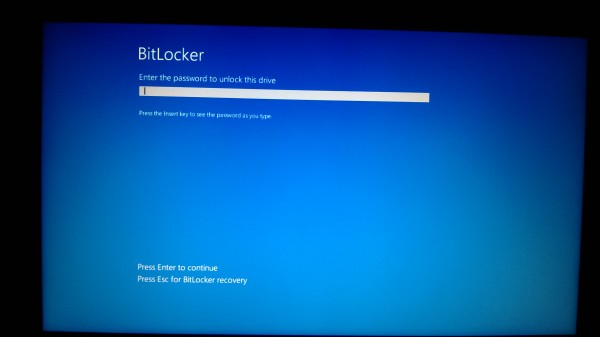
After the Enable BitLocker for Windows To Go task has ran and a reboot you need to supply your BitLocker passphrase provided in the Task Sequence Media Wizard to be able to boot into Windows To Go.
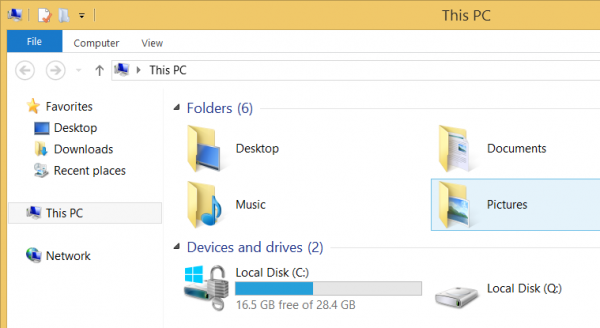
After provisioning the device and logging on you see that the “Local Disk (C:)” of the IronKey USB device is encrypted.
Like always there are more ways in doing things, another way is via PowerShell. Have a look at Mikael Nystrom his PowerShell Is King – Deploying Windows To Go devices using PowerShell blog to find out more.



Peter,
Great series of posts – really useful. Cheers!
It’s been a long time since you did them but we have found that Win2Go gives us some particular problems in ConfigMgr once it is out there in use. I figured the answers (if you had them) would be useful to anyone else who arrives here.
Because the device is constantly changing its hardware serial number, MAC address, BIOS GUID, etc., it is not so easy to keep track of it for asset management. We can probably work around this by ‘tagging’ each device somehow in the task sequence and then retrieving this through ConfigMgr inventory.
However, one problem we can’t seem to solve is that duplicate IDs are created when our users boot from the device on a corporate PC which is also in ConfigMgr. Do you know of any way to fix this or work around it?