 Microsoft has added support for Microsoft Passport for Work as an alternative sign-in method for Windows 10 users.
Microsoft has added support for Microsoft Passport for Work as an alternative sign-in method for Windows 10 users.
If users of a Windows 10 device use Active Directory or Azure Active Directory to authenticate the password, smart card or virtual smart card can be replaced for Microsoft Password. As an Intune admin you are able to configure how Microsoft Passport is going to behave. Let’s have a look!
When enabling the feature under Admin > Mobile Device Management > Windows > Windows Passport.
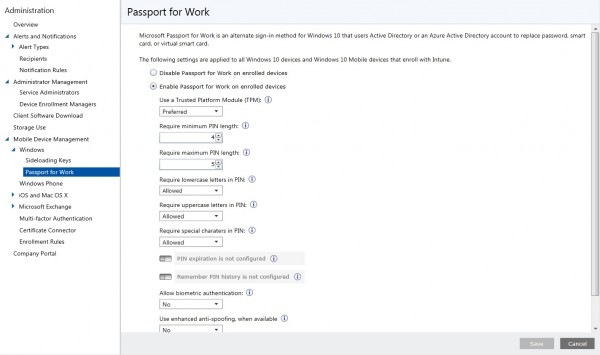
The following settings can be configured for Microsoft Password for Work:
| Setting | Setting | Description |
| Use a Trusted Platform Module (TPM) | Preferred or Required | The TMP chip provides an extra layer of data security |
| Require minimum PIN length | 4-127 | The minimum PIN length |
| Require maximum PIN length: | 4-127 | The maximum PIN length |
| Require lowercase letters in PIN: | Allowed, not allowed, Required | Configure complexity of the PIN and allow, not allow or require a PIN with lowercase letters. |
| Require uppercase letters in PIN: | Allowed, not allowed, Required | Configure complexity of the PIN and allow, not allow or require a PIN with uppercase letters. |
| Require special characters in PIN: | Allowed, not allowed, Required | Configure complexity of the PIN and allow, not allow or require a PIN with special characters. |
| PIN expiration (days): | Numeric value (41) | PIN will be expired after an X number of days |
| Remember PIN history: | Numeric value (5) | PIN will be remembered for an X number of changes. |
| Allow biometric authentication: | No/Yes | Allow biometric authentication like Windows Hellos face recognition or iris scan. |
| Use enhanced anti-spoofing, when available | No/Yes/Not configured | If not configured, users can choose to use the enhanced anti-spoofing on supported devices, or not. |
| Use Remote Passport: | No/Yes | Use Remote Passport as a portable companion device for desktop authentication. Azure AD is required. |
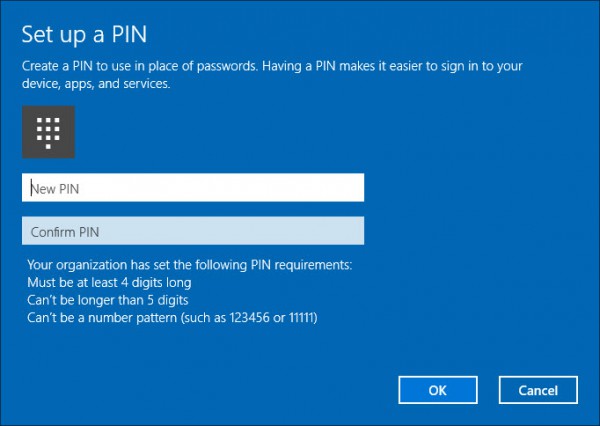
After enabling the support for Microsoft Passport the user is forced to create a PIN as configuredby the organization like shown below.
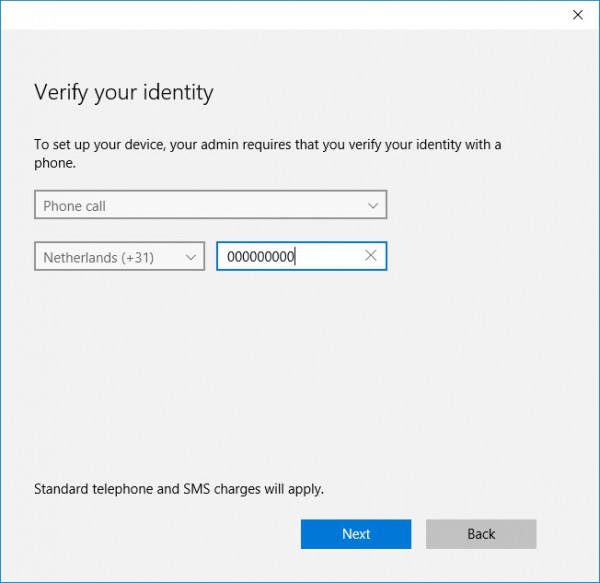
The first step is that the account/idenity needs to be verified via MFA like an SMS, a phone call or via a challenge response app from Azure AD.
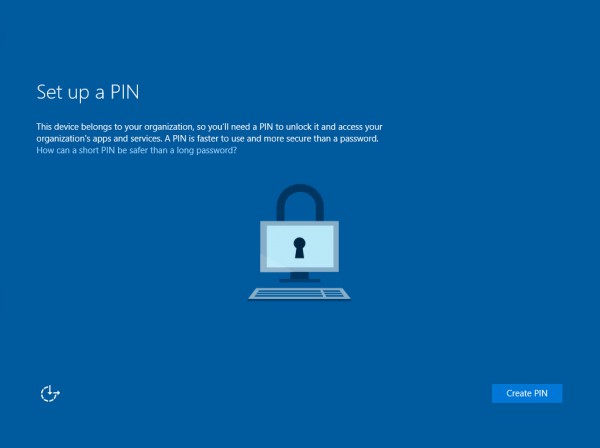
After it is all being verified a PIN can be set according to the settings configured in Microsoft Intune.
Not all tenants have already been upgraded yet, as far as I know Europe 01 and North America 01 are and the current version number of Intune can be found here.



Hi,
I was trying to test PassportforWork CSP for Windows 10 Enterprise and enabled it via intune with latest UI. i can see the changes get pushed to registry but i don’t see the above screen where it asks user to set the PIN. when will this screen appear after system restart or as notification. I am testing this on a VM managed by MDM and joined with AAD for my tenant.
Any help in this regard is appreciated
Thanks,
Reenu