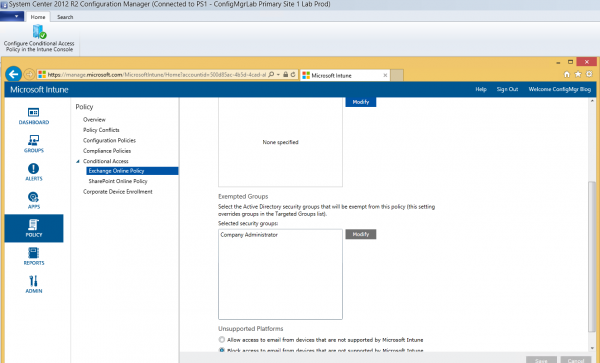
 Yesterday announced and today a new Intune Extension for Configuration Manager 2012 R2 was available. The extension enables us to set up conditional access for customers using Exchange Online, you are able to restrict Exchange ActiveSync for users that have their devices enrolled.
Yesterday announced and today a new Intune Extension for Configuration Manager 2012 R2 was available. The extension enables us to set up conditional access for customers using Exchange Online, you are able to restrict Exchange ActiveSync for users that have their devices enrolled.
Let’s see how this works together with Exchange Online.
The first step is to enable and install the Conditional Access Extension in the Configuration Manager Console.
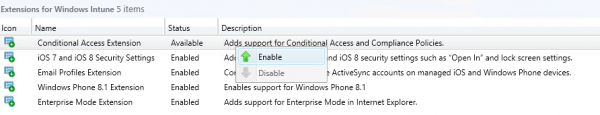
After enabling and installing the exentsion you see that two new nodes are added to the Configuration Manager 2012 R2 Console. Look below and you see Compliance Policies and Conditional Access.
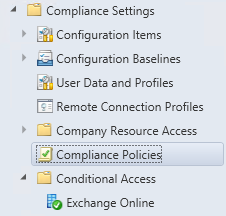
After enabling the extension you are able to create and deploy a compliance policy which is supported by the following mobile device platforms;
- Windows 8.1 and later
- Windows Phone 8.1 and later
- iOS 6.0 and later
- Android 4.0 and later
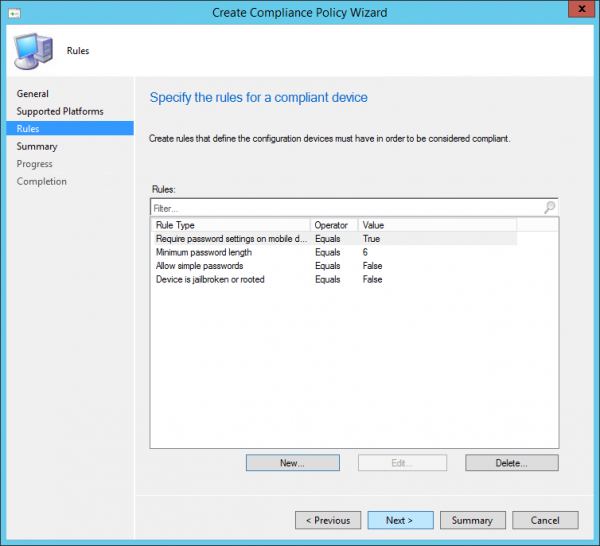
Depending on the device type we are able to configure rules that can be remediated or not before access to Exchange Online is permitted;
Windows 8.1 and later:
- PIN or password configuration can be remediated
Windows Phone 8.1 and later:
- PIN or password configuration can be remediated
- Device encryption can be remediated
iOS 6.0 and later:
- PIN or password configuration can be remediated
- Device encryption can be remediated by setting also PIN
- Jailbroken device can be placed in quarantine
- Email profile must be managed via Intune, if not the device is placed in quarantine
Android 4.0 and later:
- PIN or password configuration can be placed in quarantine
- Device encryption can be placed in quarantine
- Jailbroken device can be placed in quarantine
Let’s see how we are able to configure a Conditional Access Policy and how we are able to deploy it to a device that is managed via Configuration Manager 2012 R2 that is connected to Microsoft Intune. First we need to create a Compliance Policy to configure in this demo.
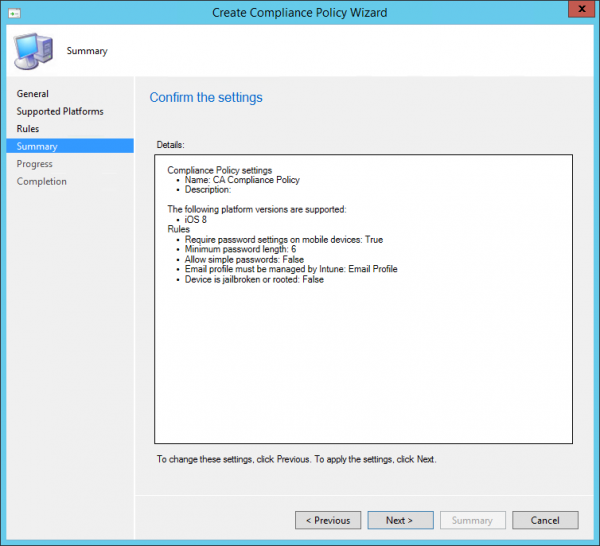
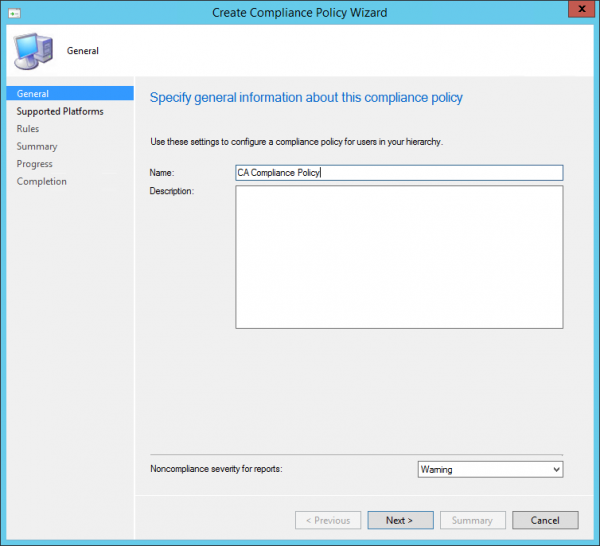
Let’s first give the Compliance Policy a name.
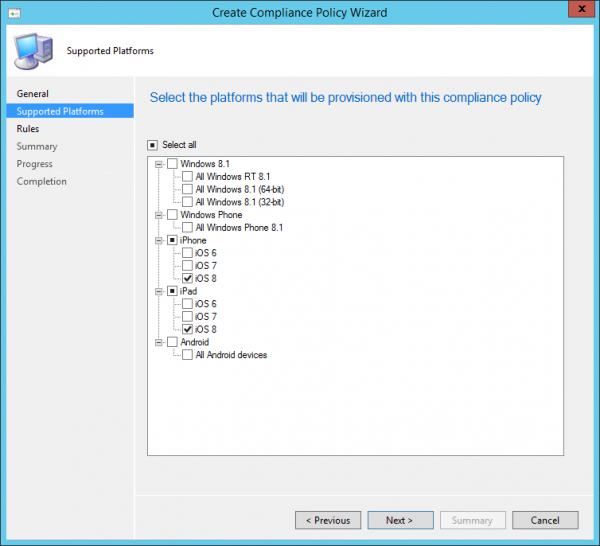
Select the Supported Platforms, in this case iPad iOS8
Next you need to configure the compliance settings for the device. The device must be compliant before access to Exchange Online is approved.
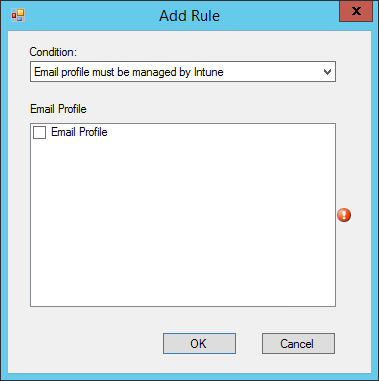
You can add the managed email profile so that the devices are checked if this profile has been installed and if it is managed by Intune.
Next you can review the settings and click next to create the policy.
After the compliance policy is created you need to deploy it via Configuration Manager.
The next step is that you need to setup Conditional Access in Microsoft Intune, so you need to logon with your tenant admin.
Enable Block mail apps from accessing Exchange Online if the device is incompliant and configure the (Synced AD) groups that needs to be targeted with the conditional access.
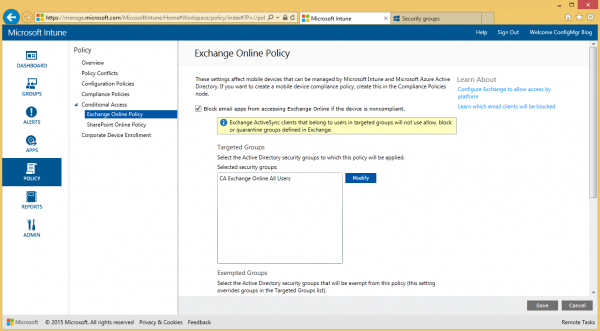
And configure the groups of users that are allowed to be incompliant.
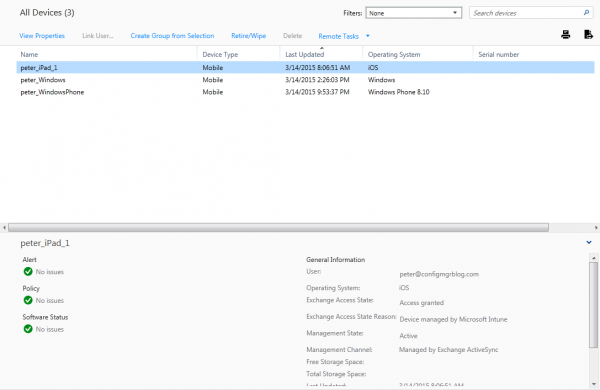
A quick look at the iPad that received the Compliance Policy.
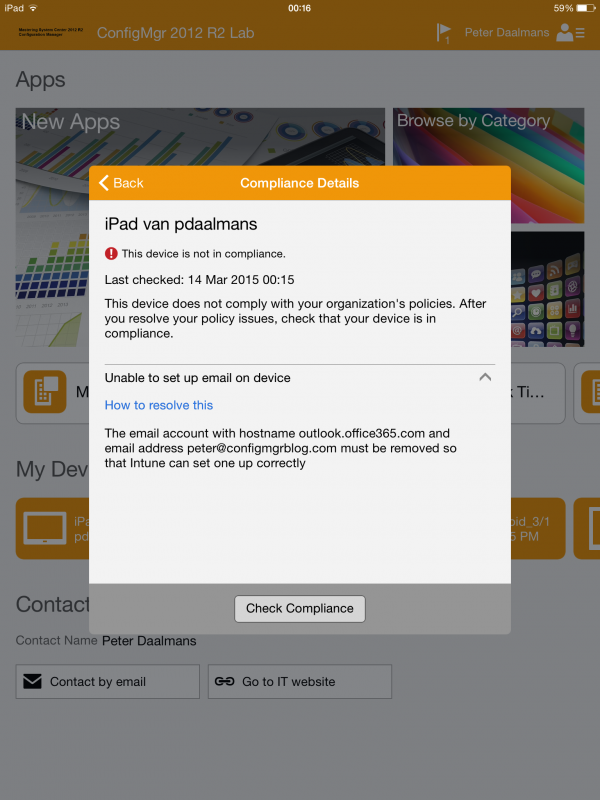
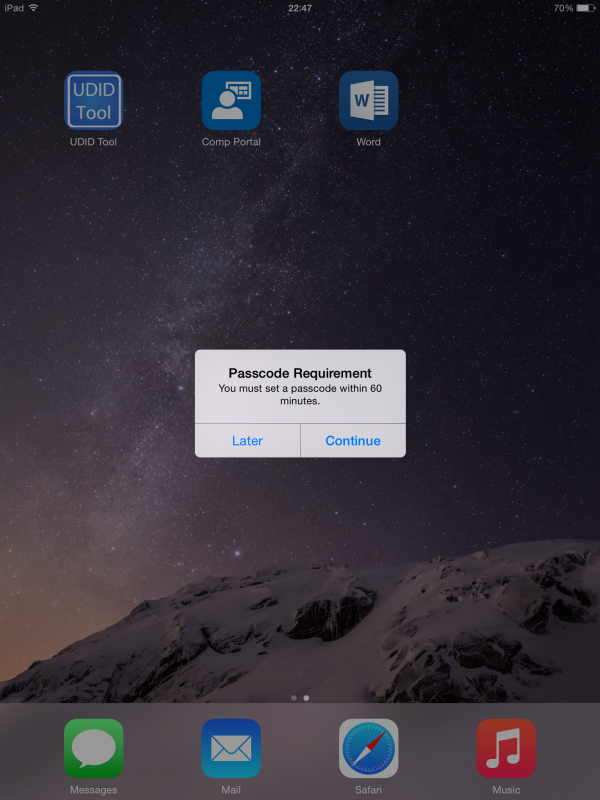
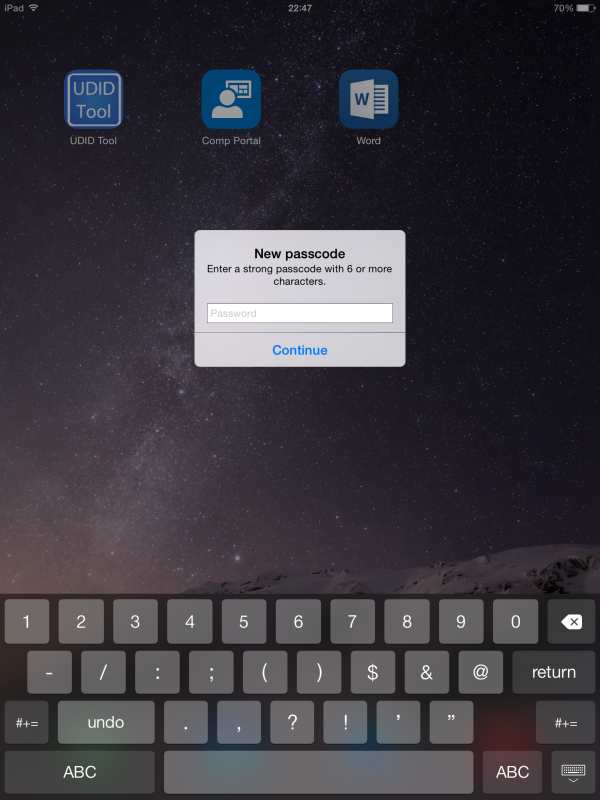
And of course when the device is not enrolled or compliant you will not be able to synchronize your email!
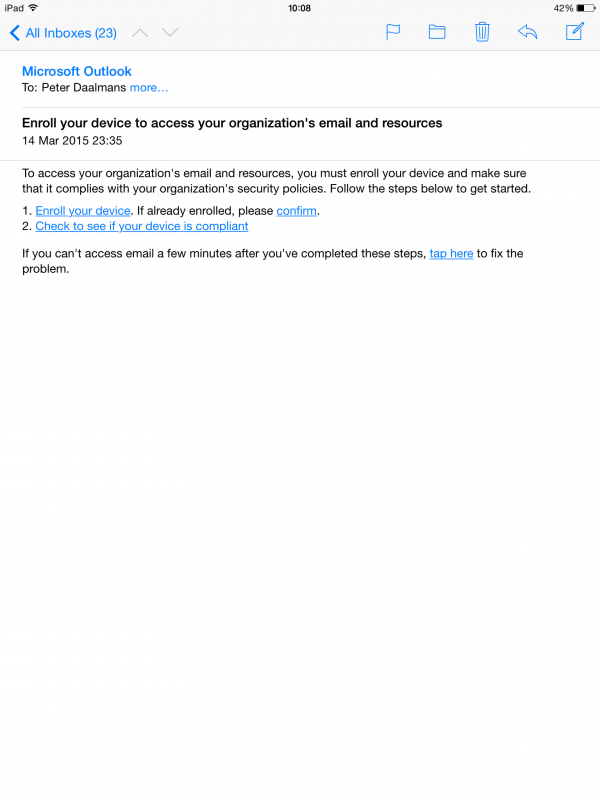
Microsoft Intune side
When looking back at Microsoft Intune you see that three Exchange Devices are placed in Quarantine.
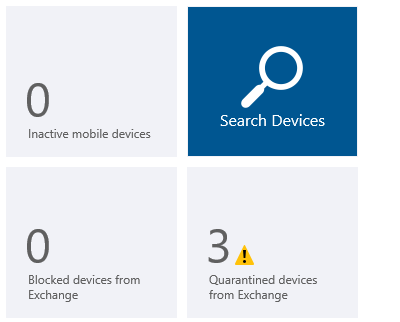
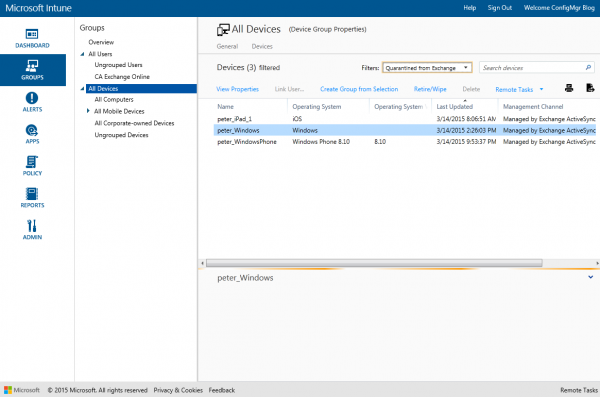
When you select one of the devices that are in quarantine you see why the device is in quarantine. The device called peter_iPad_1 is in quarantine because the Device is not managed by Microsoft Intune.
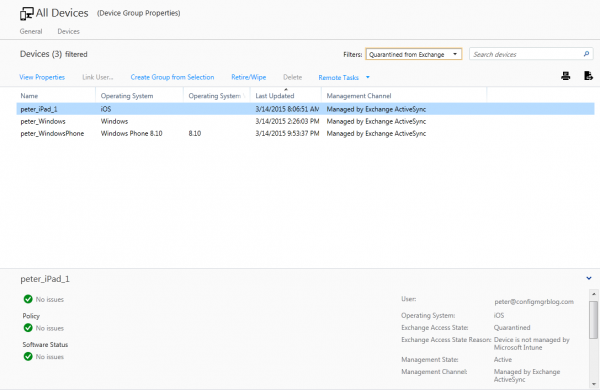
After the device is compliant you see that the device is not in quarantine anymore. Access is granted and managed by Microsoft Intune.