 We have looked in this series of blogs at the architecture, how the integration needs to be configured, and we looked at the admin and end user experience. Next subject is how to enable support for Lookout for Work on iOS devices. (see links to earlier blogs at the bottom of this blog)
We have looked in this series of blogs at the architecture, how the integration needs to be configured, and we looked at the admin and end user experience. Next subject is how to enable support for Lookout for Work on iOS devices. (see links to earlier blogs at the bottom of this blog)
It’s a bit different than when using Lookout for Work for Android devices, for Android the app is available in the Google Play store, for iOS the app is not available in the Apple App store.
The security on Apple iOS devices is way different than on Android devices, apps installed from the Apple App store can almost access nothing in the iOS Operating System. For an anti-virus / malware solution this can be an issue since you need access to for instance apps that are installed to see if there are any threats on the mobile device. To be able to do so you need to download the Lookout for Work IPA file from the Lookout website and sign it with your own Apple Developer certificate and you need to own a Mac OS X device.
Preparing Apple Developer
Before we can sign the Lookout for Work app we need to setup the Apple Developer part, this part consists of registering an App ID and setting up a Provisioning Profile. Of course we need also iOS Distribution certificate.
To create all of this you need to be part of the Apple Developer Enterprise Program, a paid subscription which allows you to create apps or sign apps for the Apple platforms. You need to go to https://developer.apple.com and sign your company up for this program. After this is completed you can create an In-House and Ad Hoc certificate so that you can sign Lookout for Work for In-House or for Ad Hoc distribution.
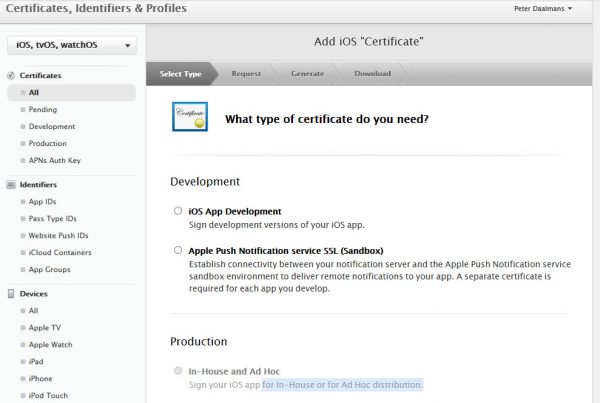
In above figure the option In-House or for Ad Hoc because you can only create to In-House or for Ad Hoc certificates per account. You can use the certificate for more apps than Lookout for Work only.
Next you need to create an App-ID, supply a name (like Lookout for Work EMS), a App-ID (like com.lookout.enterprise.ems) and click continue since no extra app services need to be added.
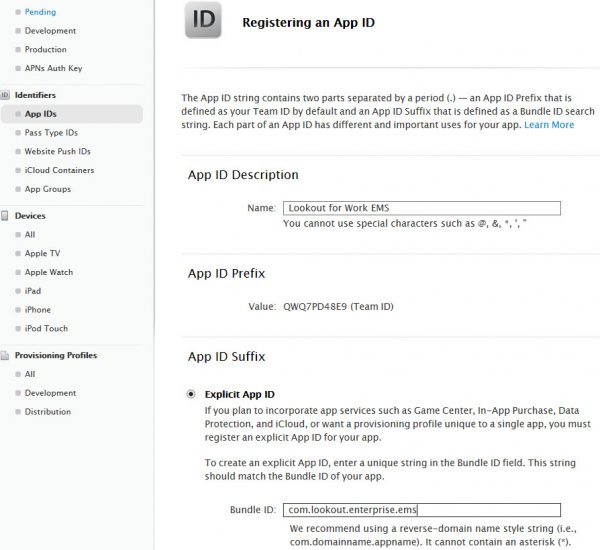
After reviewing the settings, click Register to register the App-ID.
The last part of preparing the Apple developer part is to create an iOS Distribution Profile. Click the Plus sign in the Provisioning Profiles section of the Apple Developer portal. Create the Provisioning profile as follows:
- Type: Distribution > In House
- App ID: com.lookout.enterprise.ems (like you have created earlier)
- Certificate: select the right IOS Distribution certificate
Supply a name for the Distribution Profile and download it to your device. You will need this profile while signing the Lookout for Work app.
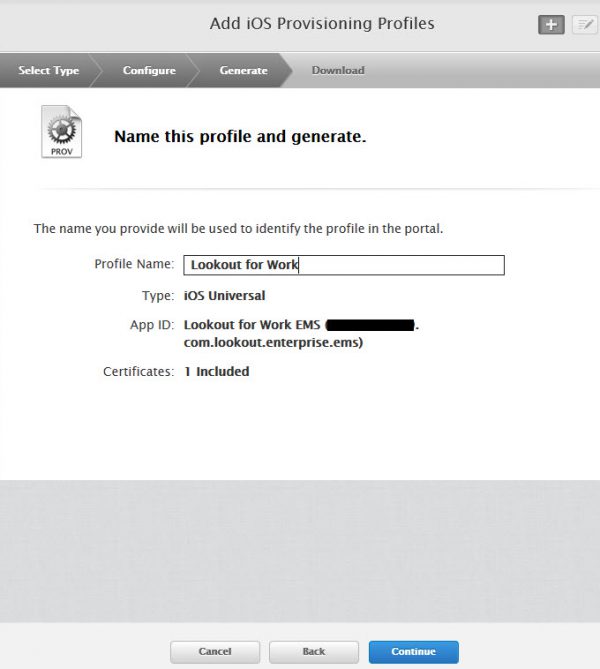
Downloading and signing the app
After logging in to the Lookout portal we need to download the latest version of the IPA file of Lookout for Work and the Lookout IPA Signing Tool for OS X to your Mac OS X device. Don’t forget to also install the Xcode Command Line Tools.
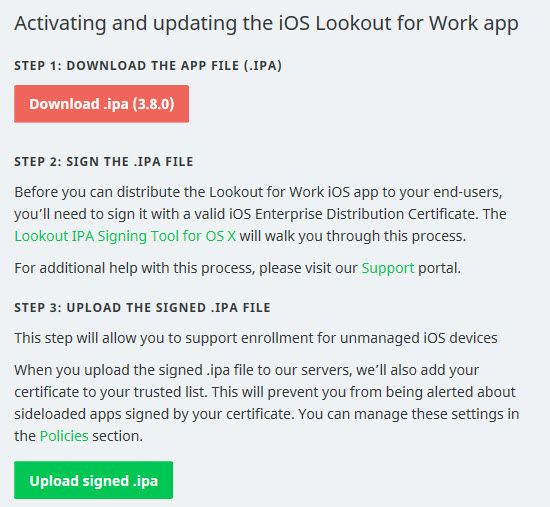
After downloading the IPA file we need to sign the App and make it ready for deployment via Microsoft Intune so start the download Lookout IPA Signing Tool.
- Select the downloaded IPA file and click Next
- Select the Mobile Provisioning profile
- Enter the bundle ID
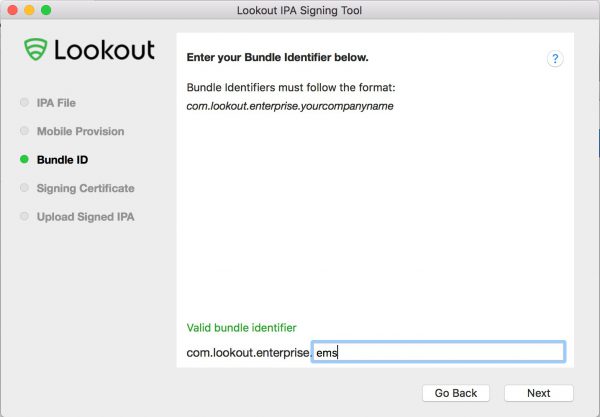
- Select your companies Signing Certificate
- Save the singed IPA
Last step is uploading the IPA via the Lookout console, when doing this you will automatically see when a newer version of the IPA is available and until when the IPA is valid.

Create Azure AD Application for IOS version of Lookout for Work
So now that the IPA file has been signed we need to create an application for Lookout for Work in Azure Active Directory.
- Go to https://portal.azure.com
- Go to Active Directory >> App registrations
- Click Add
- Supply an app name, set the application type to Native and configure the redirect URI as follows; the redirect URI needs to have the following format: lookoutwork://com.lookout.enterprise.<yourcompanyname> In this example we are going to use lookoutwork://com.lookout.enterprise.ems as shown in the figure below;
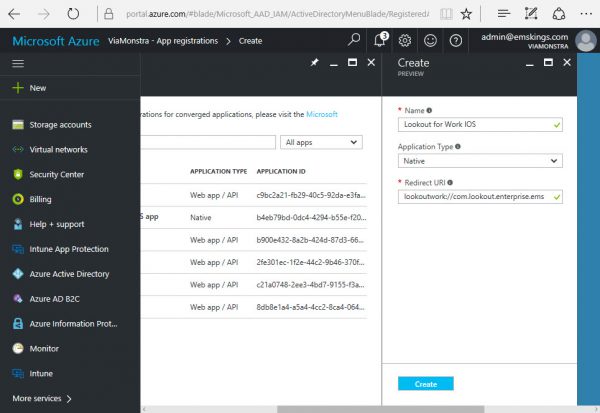
- Click Create. Next open the created app and add another redirect URI with the following syntax; companyportal://code/lookoutwork%3A%2F%2Fcom.lookout.enterprise.<yourcompanyname> In this example we are going to use companyportal://code/lookoutwork%3A%2F%2Fcom.lookout.enterprise.ems as shown in the figure below;
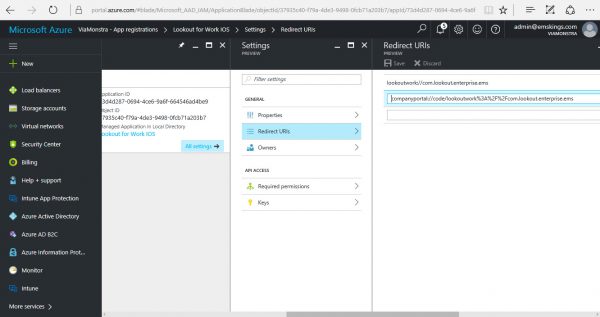
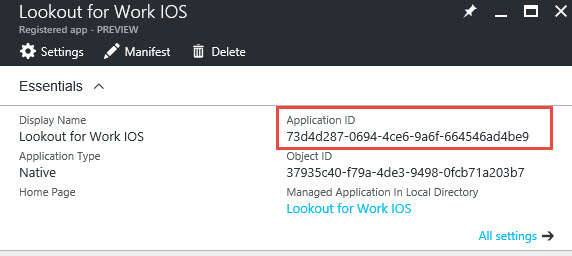
- Next we need to document the Application ID of the Registered app, we need this one in Microsoft Intune
- Last part of configuring the Azure Application is to set the permissions to other applications. In the Required Permissions node of the Azure Application you need to add the following permissions; API: Lookout MTP Permissions: Access Lookout MTP API: Microsoft Graph Permissions: Sign in and read user profile
Enabling iOS Synchronization with MTP and deploying the app with Microsoft Intune
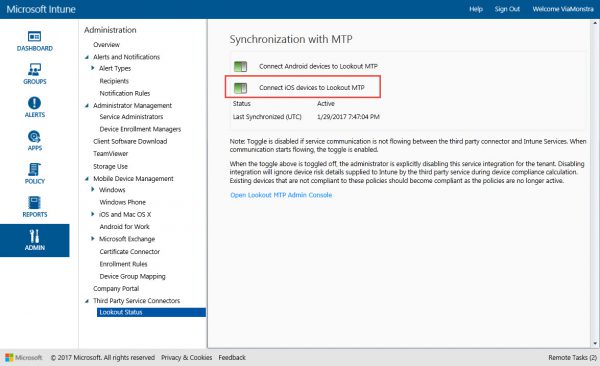
First let’s enable the connection between Intune and the iOS devices and Lookout MTP. In the administrator node of the Microsoft Intune console you are able to enable the switch for iOS in the Third Party Service Connectors >> Lookout Status node.
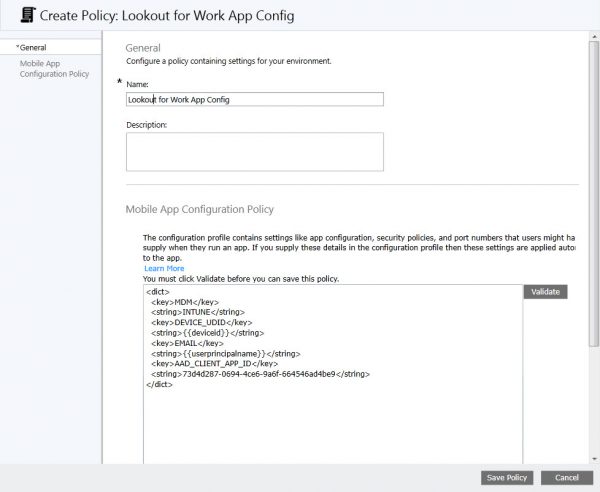
Next we need to add the signed App to Microsoft Intune and create a Mobile Application Configuration Policy. In the XML code, shown below you need to replace <APP-ID> with the application ID you documented earlier.
<dict>
<key>MDM</key>
<string>INTUNE</string>
<key>DEVICE_UDID</key>
<string>{{deviceid}}</string>
<key>EMAIL</key>
<string>{{userprincipalname}}</string>
<key>AAD_CLIENT_APP_ID</key>
<string><APP-ID></string>
</dict>
The last part is deploying the Azure Microsoft Authenticator app and the signed Lookout for Work app, with the Mobile Application Configuration to the iOS devices. After the apps are installed and activated you are compliant and protected by Lookout for Work.
In the next and last blog in this series we will have a look at the integration of Lookout in a Hybrid scenario, remember to be able to use the integration of Lookout with Intune you need a separate Lookout MTP license.
Other blogs in this series:
- Integration Microsoft Intune and Lookout Mobile Threat Protection is there
- Intune and Lookout: the architecture of the integration
- Intune and Lookout: how to integrate?
- Intune and Lookout: the admin experience.
- Intune and Lookout: the end user experience.
- Intune and Lookout: supporting iOS devices
- Intune, ConfigMgr and Lookout better together



Apple developer account has 3 versions: individual program, company program and enterprise program. We need to buy or rent the enterprise account, if you have, please contact us.