It has been a while after I started this blog series about Intune and Lookout. (see at the bottom of this page the earlier blogs)
It has been a while after I started this blog series about Intune and Lookout. (see at the bottom of this page the earlier blogs)
Today I had finally time to write about the next subject in this series; the end user experience. Since I will dedicate a blog about the iOS version of the app, this blog will only about the experience on Android devices.
For Android you just need to deploy the Lookout for Work app from the Google Play store and deploy it mandatory so that the user can install the app on the Android device. To become compliant, the user needs to install and activate the app with the UPN of the user.
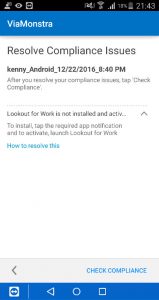
So after enabling the compliance policy or after enrolling a new device the user need to install and activate Lookout for Work. After starting Lookout for Work you need to activate the via Azure Active Directory, as explained earlier the device compliance state is stored in Azure Active Directory.
[table style=”1″] [tr][td]

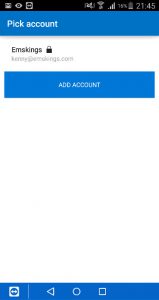

When the Azure Authenticator is installed, the authenticator will be launched so that you can select the UPN of the user.
After activating Lookout and connecting to the Lookout service a first scan is initiated to be sure that the device is secure. The Google Play store is unfortunately full of applications that contain malicious code or are just Trojans or viruses. To test if everything is working we can install the test virus Eicar and see what happens.
[table style=”1″] [tr][td]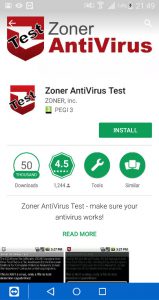
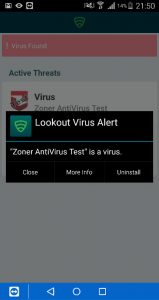
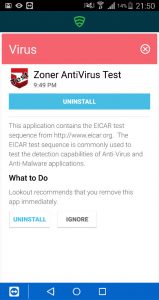
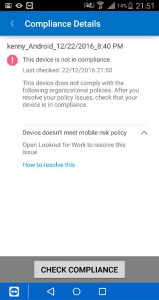
The virus is detected and the user needs to remove the bad application to become compliant again, as you see below the device is marked as not compliant instantly.
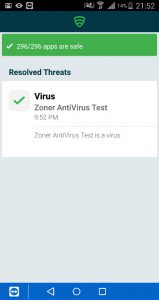
After removing the bad application the device will be checked again and marked compliant again.
Troubleshooting
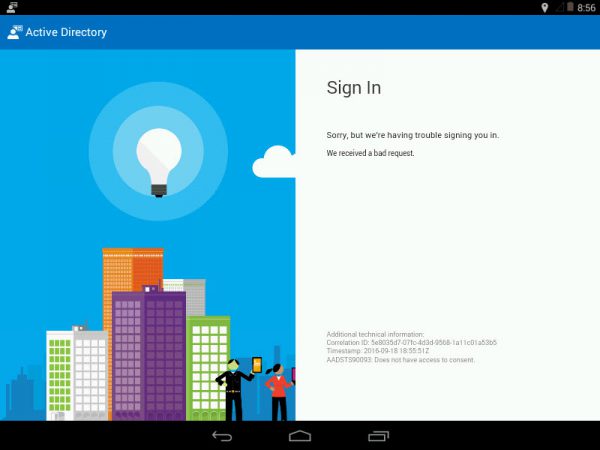
When your users receive an error like the following while activating the Lookout for Work app;
AADSTS90093: Does not have access to consent.
The users are not allowed to configure the consent themselves due to organizational settings in Azure Active Directory.
Check how the UserPermissionToUserConsentToAppEnabled is configured via the following PowerShell command;
Get-MsolCompanyInformation|FL DisplayName UserPermissionToUserConsentToAppEnabled
If this is set to FALSE you need to configure the consent as a Global Administrator of Azure Active Directory.
Solution is going to this URL to configure the consent for the Lookout for Work Android app. Use for the Lookout for Work iOS app or any other app using this link: https://login.microsoftonline.
You can get the client id from Azure Active Directory.
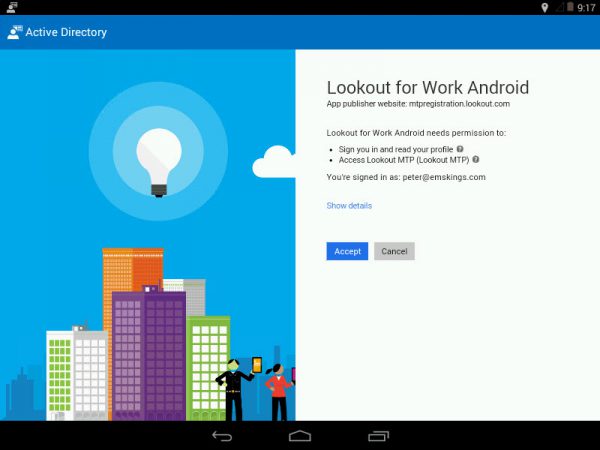
Logon with one of your Global Administrators and Accept the consent with Mozilla Firefox or Google Chrome and click Accept.
After this is done, users are able to activate Lookout for Work.
In the next blog we will have a look at the support of iOS devices, remember to be able to use the integration of Lookout with Intune you need a separate Lookout MTP license.
Other blogs in this series:
- Integration Microsoft Intune and Lookout Mobile Threat Protection is there
- Intune and Lookout: the architecture of the integration
- Intune and Lookout: how to integrate?
- Intune and Lookout: the admin experience.
- Intune and Lookout: the end user experience.
- Intune and Lookout: supporting iOS devices
- Intune, ConfigMgr and Lookout better together